> Bytes
These are byte sized posts with a simple illustration.
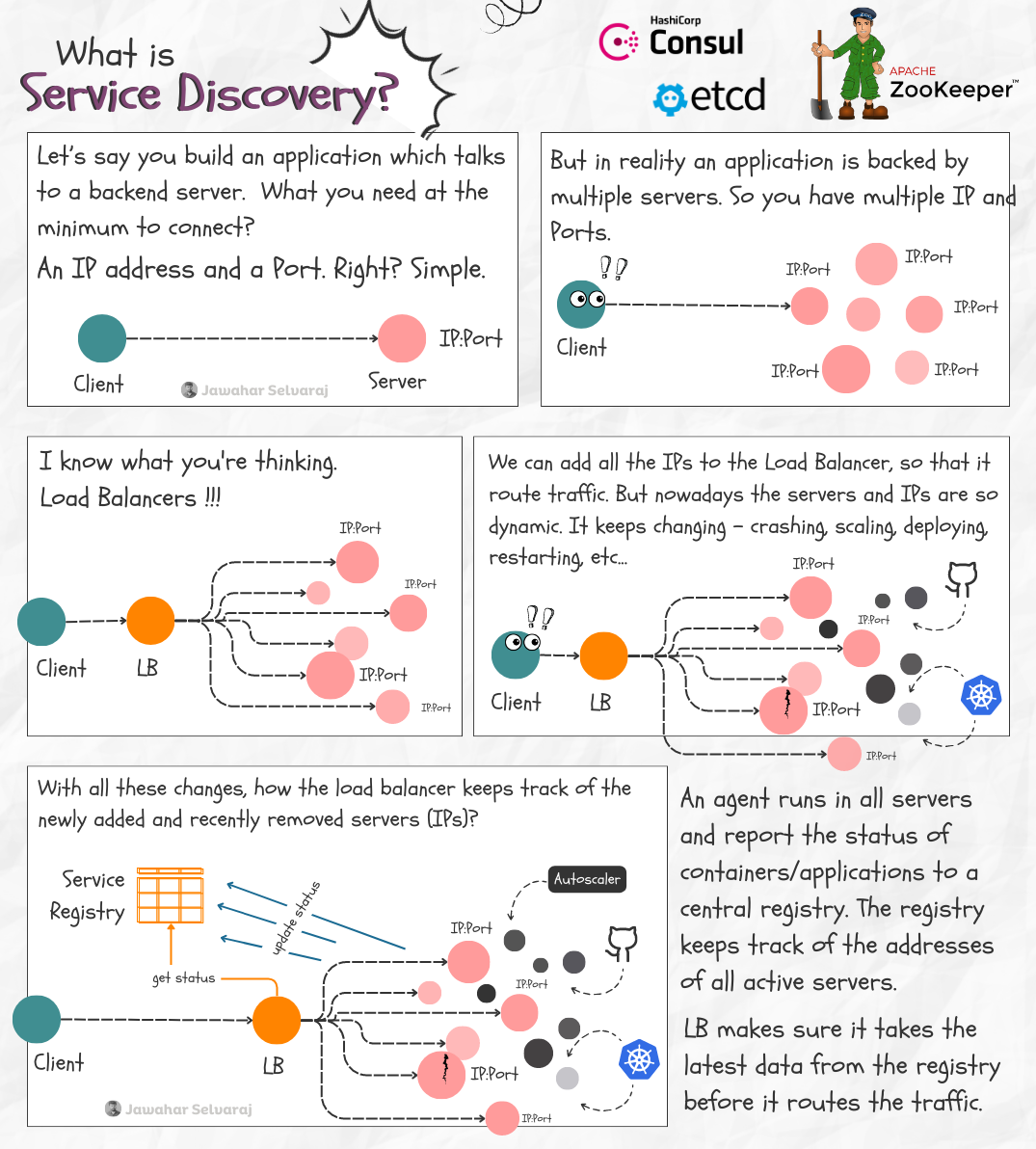
What is Service Discovery? 🏷️
Let’s say you build an application which talks to a backend server. What you need at the minimum to connect? An IP address and a Port. Right? Simple. But in reality an application is backed by multiple servers. So you have multiple IP and Ports.
[expand]
I know what you’re thinking. Load Balancers !!!
We can add all the IPs to the Load Balancer, so that it route traffic. But nowadays the servers and IPs are so dynamic. It keeps changing - crashing, scaling, deploying, restarting, etc… With all these changes, how the load balancer keeps track of the newly added and recently removed servers (IPs)? So we need a way to keep track of all the servers and their IPs. That’s where Service Discovery comes in.
An agent runs in all servers and report the status of containers/applications to a central registry. The registry keeps track of the addresses of all active servers. LB makes sure it takes the latest data from the registry before it routes the traffic.
[/expand]
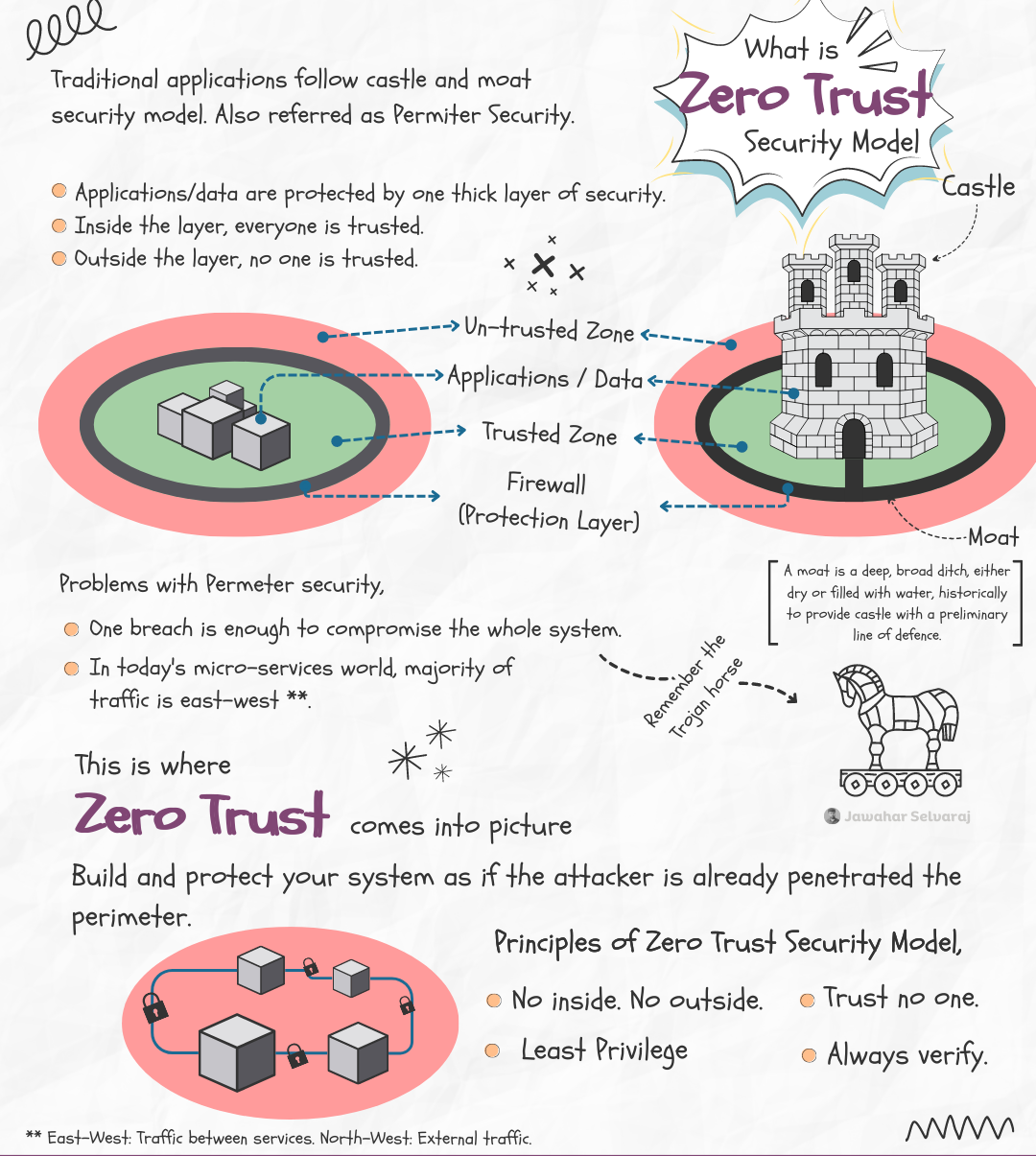
What is Zero Trust security model? 🏷️
Traditional applications follow castle and moat security model. Also referred as Perimeter Security. Applications/data are protected by one thick layer of security. Inside the layer, everyone is trusted. Outside the layer, no one is trusted.
[expand]
Problems with Permeter security,
- One breach is enough to compromise the whole system.
- In today’s micro-services world, majority of traffic is east-west **.
This is where, zero trust comes into picture. Build and protect your system as if the attacker is already penetrated the perimeter.
Principles of Zero Trust Security Model,
- No inside. No outside.
- Trust no one.
- Least Privilege
- Always verify.
** East-West: Traffic between services. North-West: External traffic.
[/expand]
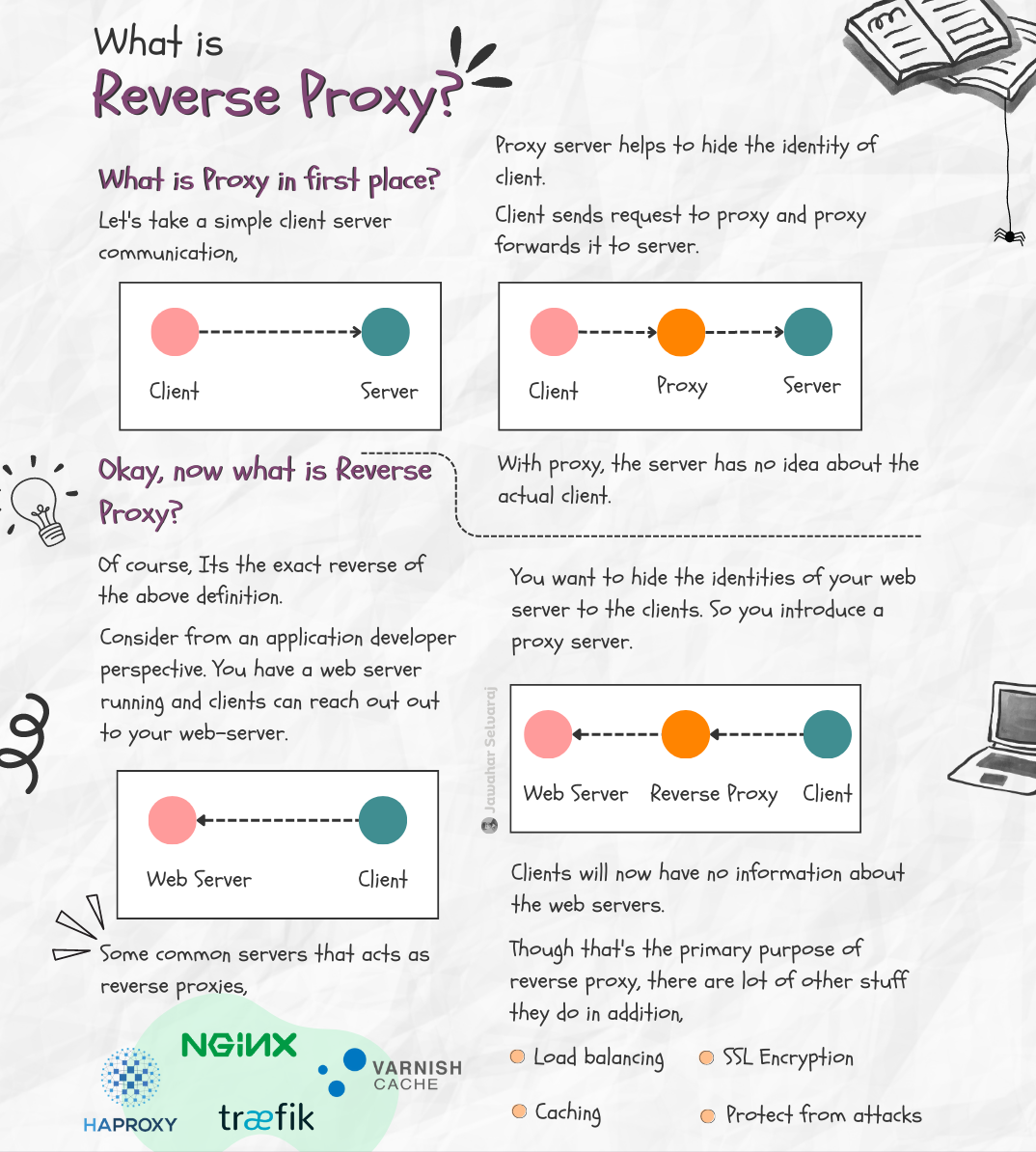
What is Reverse Proxy? 🏷️
What is Proxy in first place?
Let’s take a simple client server communication. Proxy server helps to hide the identity of client. Client sends request to proxy and proxy forwards it to server. With proxy, the server has no idea about the actual client.
[expand]
Okay, now what is Reverse Proxy?
Of course, Its the exact reverse of the above definition. Consider from an application developer perspective. You have a web server running and clients can reach out out to your web-server. You want to hide the identities of your web server to the clients. So you introduce a proxy server. Clients will now have no information about the web servers. Though that’s the primary purpose of reverse proxy, there are lot of other stuff they do in addition.
- Load balancing
- Caching
- SSL Encryption
- Protect from attacks
Some common servers that acts as reverse proxies - Nginx, Varnish, HAProxy and traefik.
[/expand]
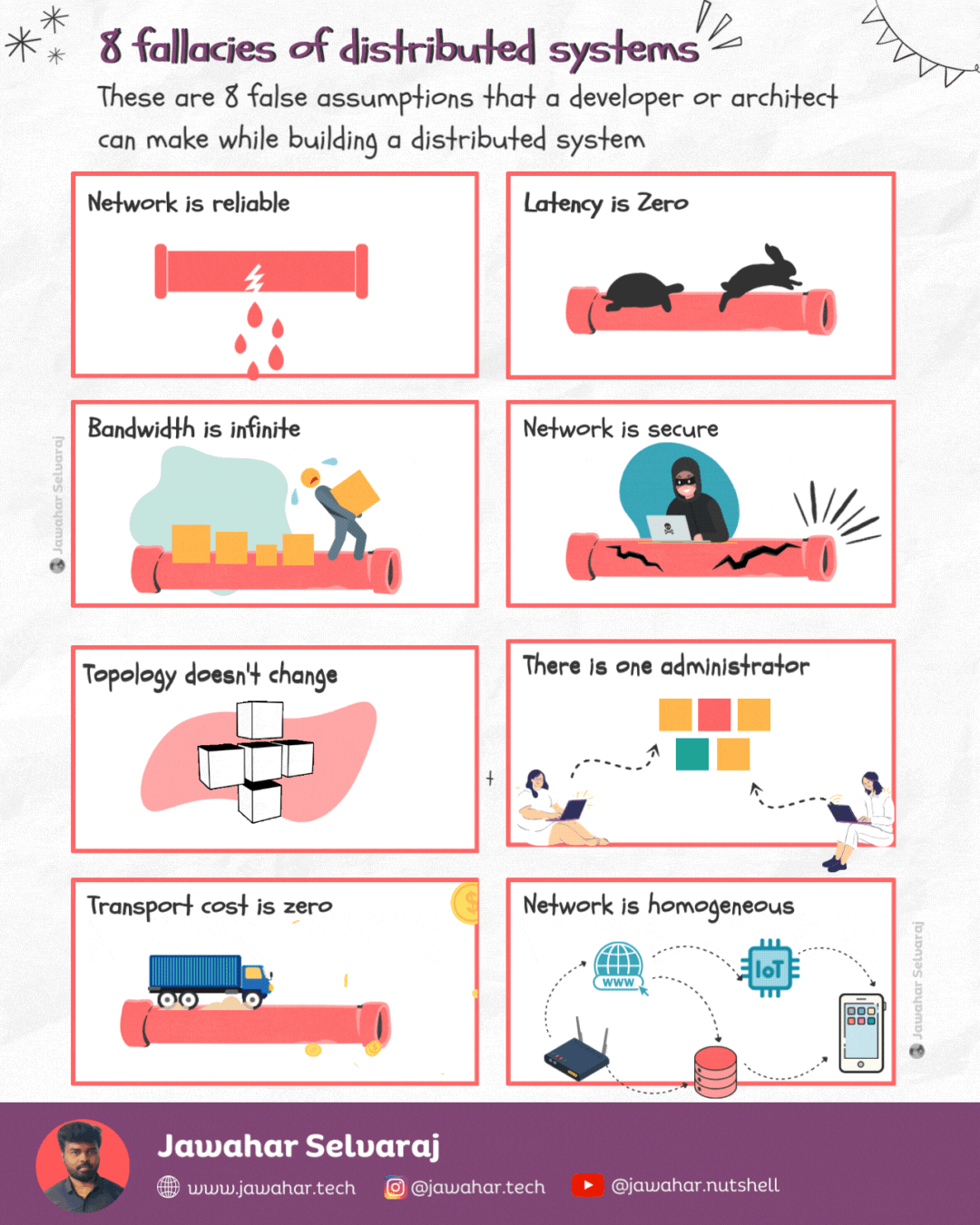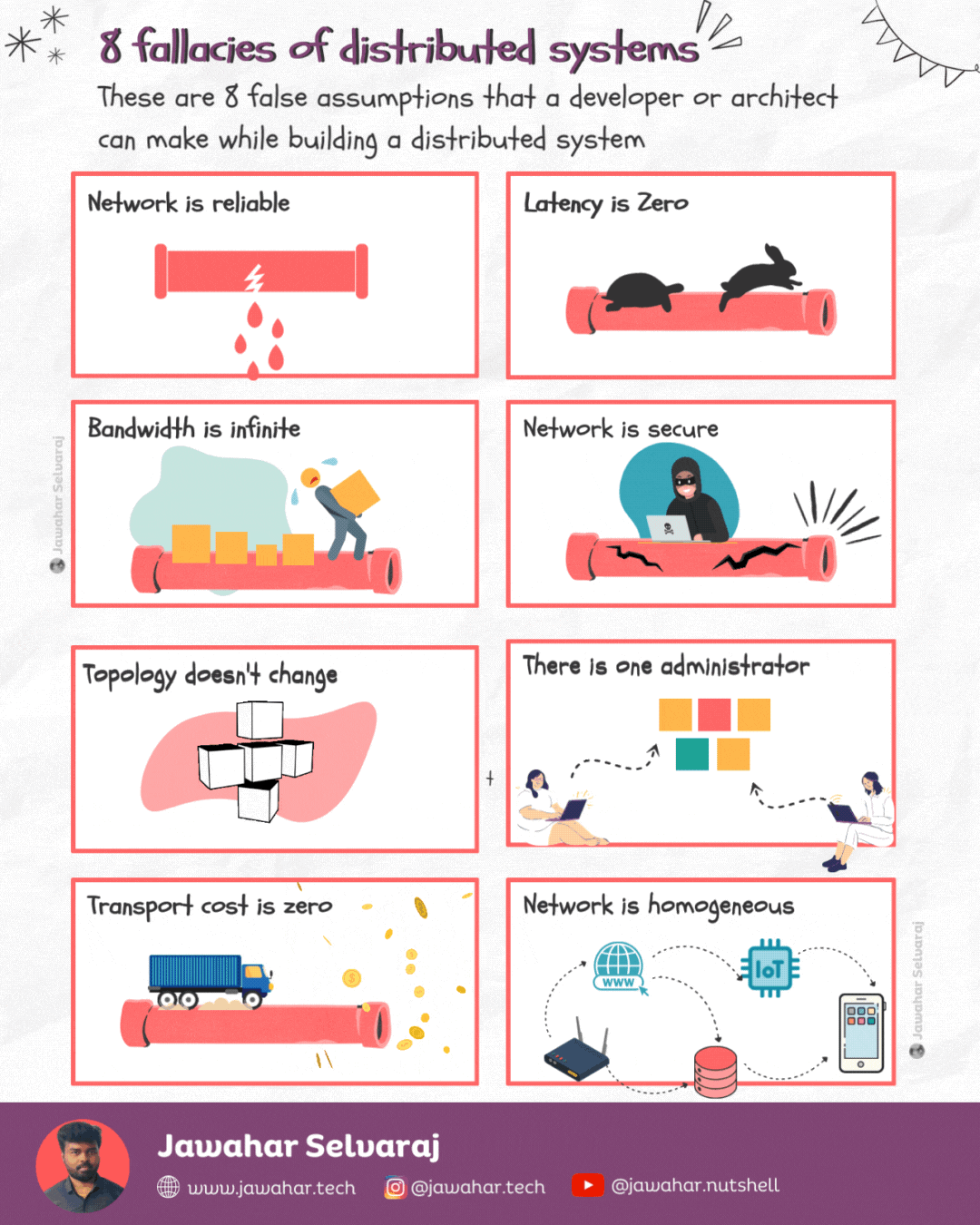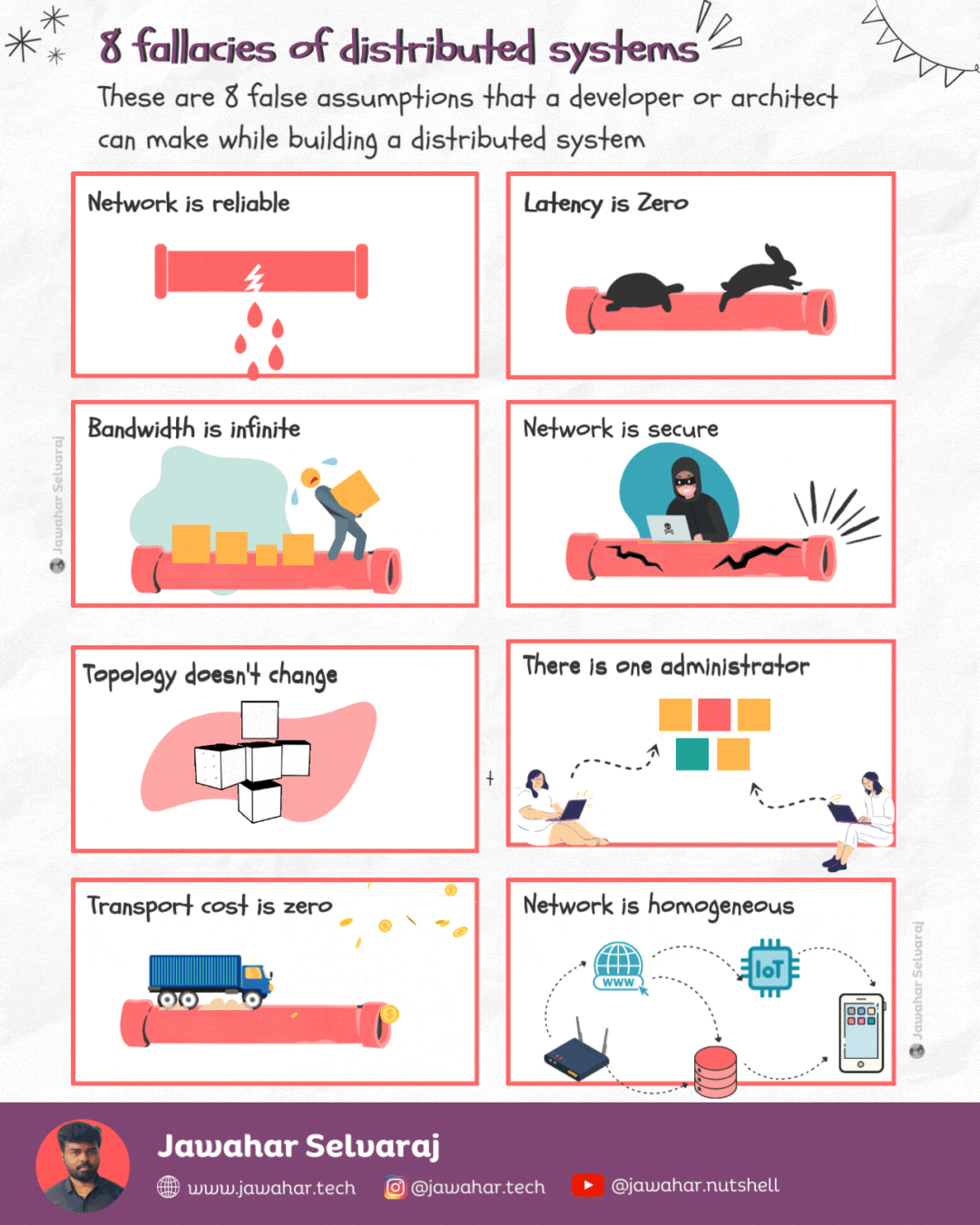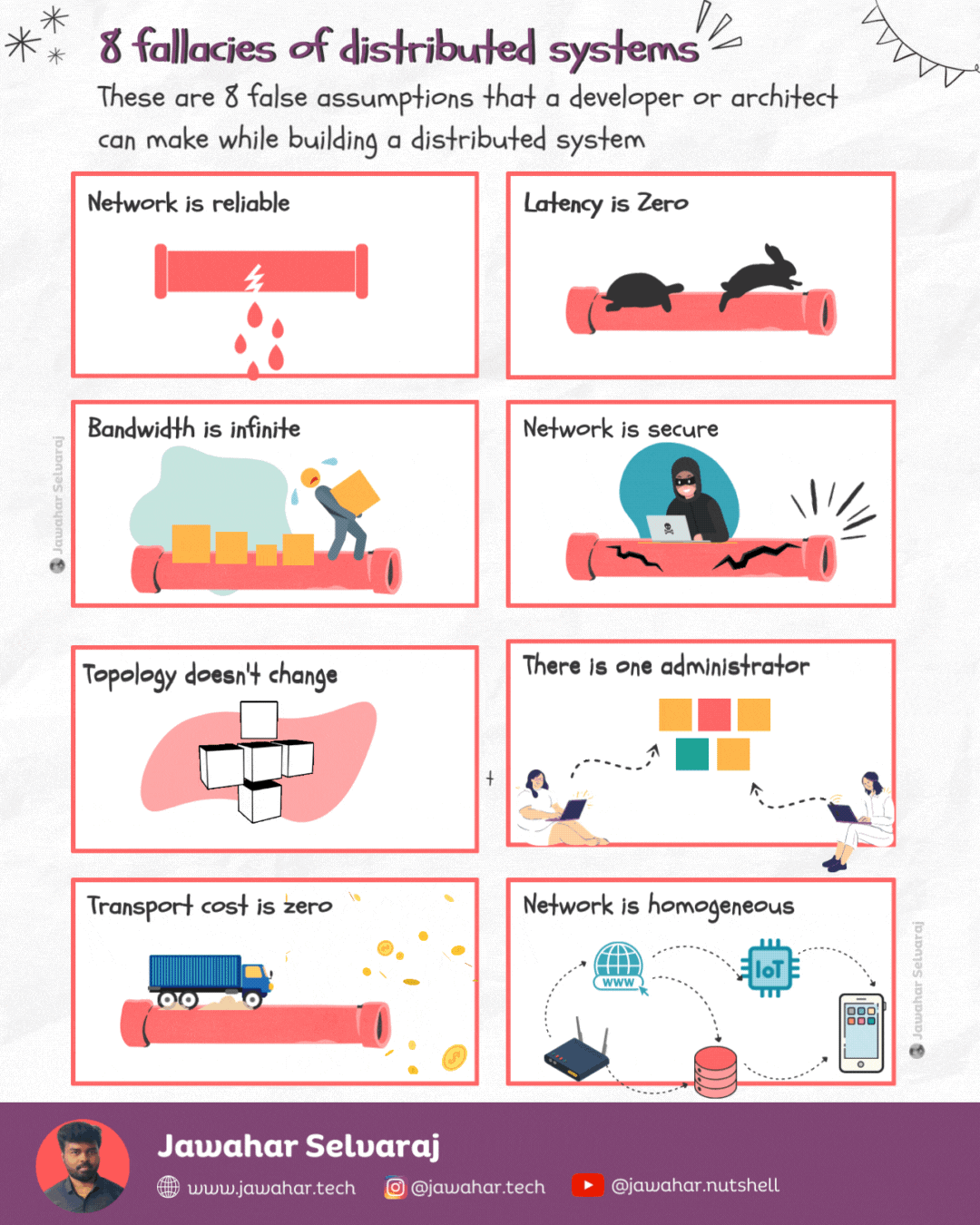
Fallacies of distributed computing 🏷️
These are the 8 false assumptions that programmers or architects make while designing distributed systems.
1.Network is reliable
Networks are complex, dynamic and often unpredictable. Many reasons could lead to a network failure or network-related issues.
[expand]
2.Latency is zero
Latency is primarily constrained by distance and the speed of light. Of course, there’s nothing we can do about the latter. Even in theoretically perfect network conditions, packets cannot exceed the speed of light.
3.Bandwidth is infinite
Latency is the speed at which data travels from point A to point B, bandwidth refers to how much data can be transferred from one place to another in a certain timeframe. Imagine it as the size of the pipe in which the water flows. The bigger the pipe the more the bandwidth.
4.Network is secure
The only truly secure system is one that is powered off, cast in a block of concrete and sealed in a lead-lined room with armed guards — and even then I have my doubts. - Gene Spafford
5.Topology doesn’t change
In a distributed system, network topology changes all the time. Sometimes, it’s for accidental reasons or due to issues, such as a server crashing. Other times it’s deliberate — we add, upgrade, or remove servers.
6.There is one administrator
When you engineer your system, you should make it easy (well, as easy as possible) for different administrators to manage it. You also need to think about the system’s resiliency and make sure it’s not impacted by different people interacting with it.
7.Transport cost is zero
Just as latency isn’t zero, transporting data from one point to another has an attached cost, which is not at all negligible.
8.Network is homogeneous
Not even your home network is homogenous. It’s enough to have just two devices with different configurations (e.g., laptops or mobile devices) and using different transport protocols, and your network is heterogeneous.
[/expand]
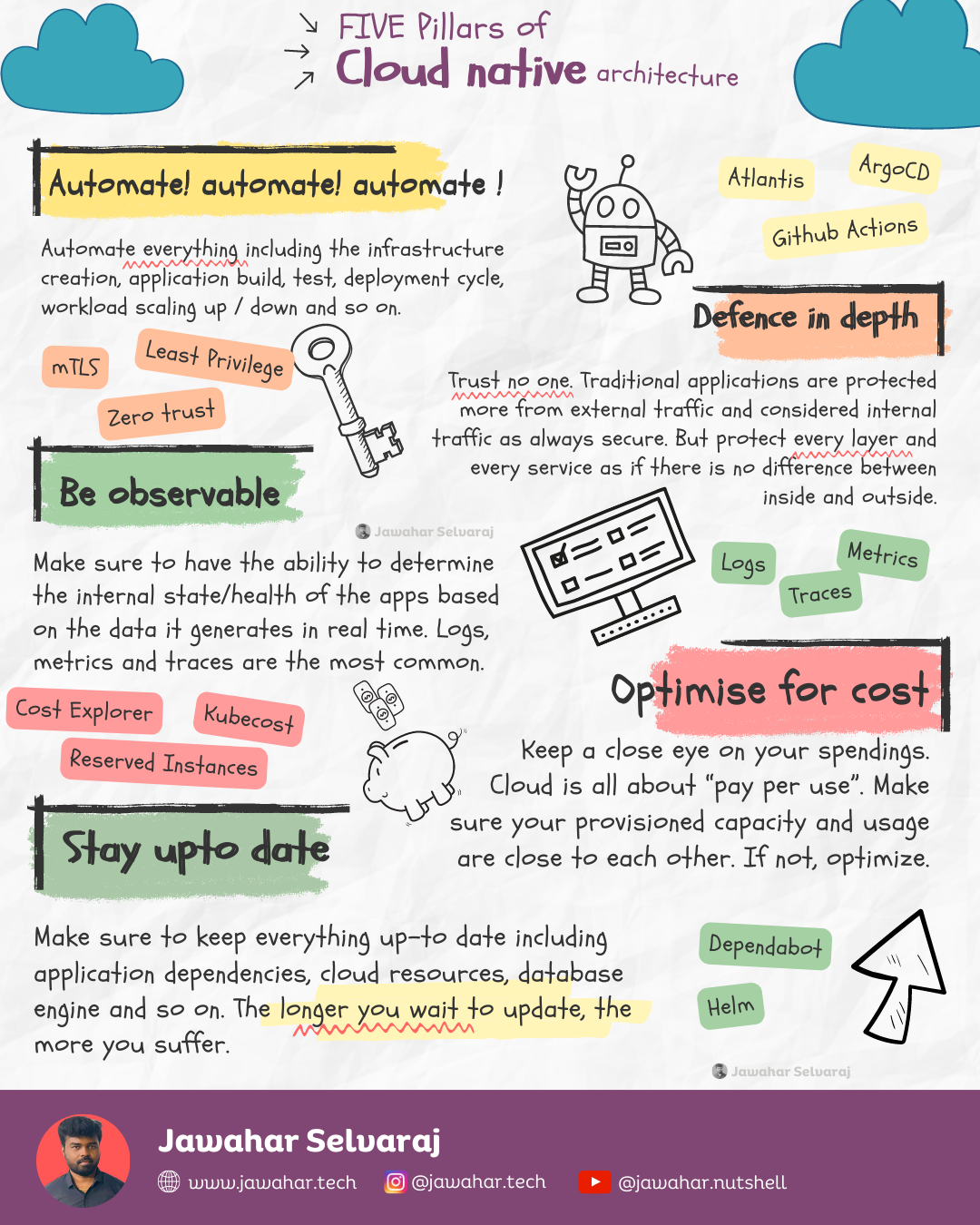
Five Pillars of Cloud Native architecture 🏷️
Automate! automate! automate !
Automate everything including the infrastructure creation, application build, test, deployment cycle, workload scaling up / down and so on.
[expand]
Defence in depth
Trust no one. Traditional applications are protected more from external traffic and considered internal traffic as always secure. But protect every layer and every service as if there is no difference between inside and outside.
Be observable
Make sure to have the ability to determine the internal state/health of the apps based on the data it generates in real time. Logs, metrics and traces are the most common.
Optimise for cost
Keep a close eye on your spendings. Cloud is all about “pay per use”. Make sure your provisioned capacity and usage are close to each other. If not, optimize.
Stay upto date
Make sure to keep everything up-to date including application dependencies, cloud resources, database engine and so on. The longer you wait to update, the more you suffer.
[/expand]
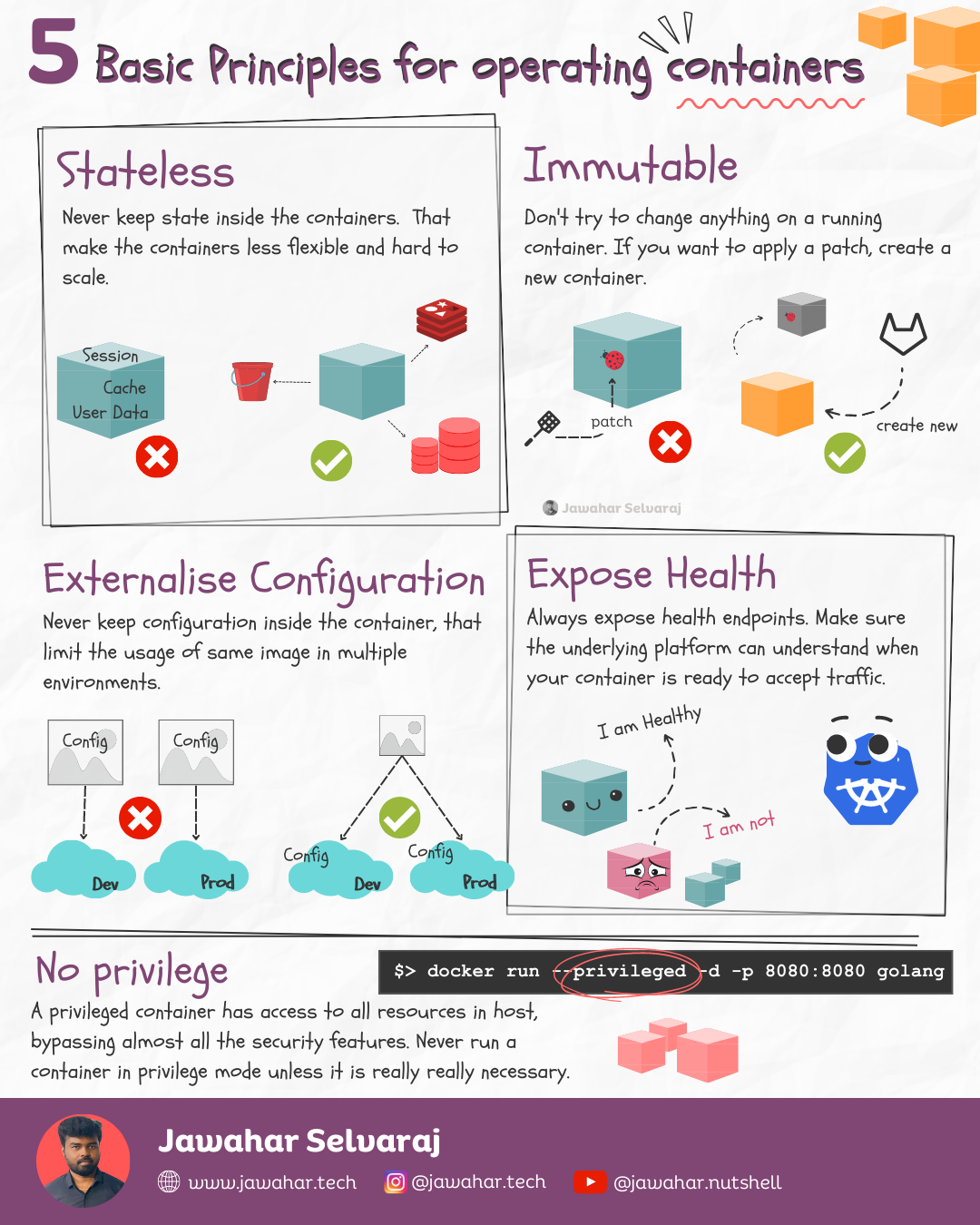
Basic Principles for operating containers 🏷️
Stateless
Never keep state inside the containers. That make the containers less flexible and hard to scale.
[expand]
Immutable
Don’t try to change anything on a running container. If you want to apply a patch, create a new container.
Externalise Configuration
Never keep configuration inside the container, that limit the usage of same image in multiple environments.
Expose Health
Always expose health endpoints. Make sure the underlying platform can understand when your container is ready to accept traffic.
No Privilege
A privileged container has access to all resources in host, bypassing almost all the security features. Never run a container in privilege mode unless it is really really necessary.
$> docker run --privileged -d -p 8080:8080 golang
[/expand]